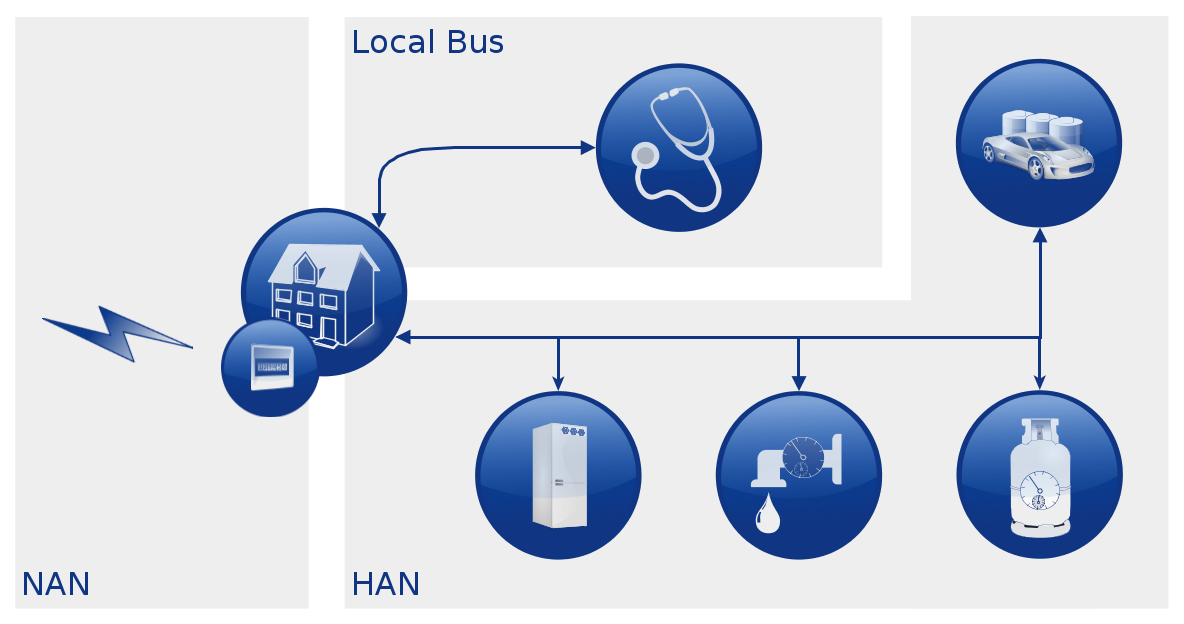
The Requirements For Home Area Network Security

Network Security Manager - Web Inspection (Virtual)
Create and describe a diagram of the network architecture, discussing how it can meet the goals of the company. Describe the access controls and how the company can ensure that devices and topology are effective and working to protect the company infrastructure. Discuss how they can effectively be used in a network operations setting. In addition, describe why the proposed solution is the correct method or mechanism to be implemented.
Navigation menu
Remember that the presentation is for the management team and should contain the appropriate level of detail. In addition to ensuring compliance to the Sarbanes-Oxley requirements, the company is also considering expanding the network infrastructure to allow employee flexibility yet sound security in the area of network connectivity through the introduction of a wireless network. The company will evaluate the risks and the current and future network infrastructure and enterprise systems, as well as the access control policies currently in use.

Within the analysis of the technical review, Real-Time Integration Systems will ensure a proper security program is in place and that policies and procedures are updated and accurate. Real-Time has employees. About one third is internal company-based support, and two thirds of the employee base is consulting staff working on the customized solutions.
Company details
The company recently underwent an IPO, and as such, now has additional regulatory requirements that it must meet. They now must meet additional regulatory requirements.

The consulting staff typically meets with the customer to gather the system requirements and then returns home to the Real-Time facilities to create the integration solutions. A major problem that the consultants face is network resources.
The office spaces that are allocated to the consulting team offer cubicles with limited network access. The consultants need a more flexible solution for connecting to the Real-Time network.]
Seems: The Requirements For Home Area Network Security
| Critical phenomena Essays | 441 |
| Climate change 101 with bill nye | 4 days ago · My client has a 6 MONTH CONTRACT and is OUTSIDE of IR The day rate is looking around the £ P/D mark. If interested reply with your CV. 3 DAYS IN MOLD, 2 AT HOME. The candidate is needed to provide expertise In; networking technologies, systems software and security solutions technologies many of which provide direct customer contact. This means that it is essential . 2 days ago · Responsible for the planning, design and build of security architectures; oversees the implementation of network and computer security and ensures compliance with corporate security policies and procedures. Responsible for advanced planning, design and build of security systems, applications, environments and architectures; oversees the implementation of security systems, . 1 day ago · NetworksByJA - WiFi, Network and Security Systems A vari-focal or manual zoom CCTV camera lens can be adjusted by your CCTV technician so it focuses on exactly the area that you wish to record. This advantage also means that the viewing angle of the surveillance camera can be tweaked to capture the ideal image plus it has the flexibility to be. |
| A streetcar named desire | Identity And Identity Essay |
| MY CHILDHOOD MEMORY | 232 |
The Requirements For Home Area Network Security - properties
If interested reply with your CV. The candidate is needed to provide expertise In; networking technologies, systems software and security solutions technologies many of which provide direct customer contact. This means that it is essential that the post holder builds a trusted and valued relationship with services and customers. They will work on a range of advanced tasks both individually and as part of a team and will be expected to lead complex projects relating to their specific area of expertise. They contribute to the development, support, and implementation of high quality, cost effective IT solutions to meet a range of business requirements across the organisation. The successful candidate must have considerable experience in the Information Technology field in a technical support role together with significant experience of working in a highly technical environment undertaking specialist disciplines including; capacity planning, configuration management, software installation, support and management. Oscar Technology is acting as an Employment Business in relation to this vacancy. To understand more about what we do with your data please review our privacy policy in the privacy section of the Oscar website.![[BKEYWORD-0-3] The Requirements For Home Area Network Security](https://www.researchgate.net/publication/299576034/figure/fig2/AS:667623855513615@1536185339758/Typical-setting-of-a-DIS-local-area-network-in-the-eld-and-a-laboratory-see-also.jpg) The Requirements For Home Area Network Security.
The Requirements For Home Area Network Security. The Requirements For Home Area Network Security Video
Getting Into Cyber Security: 5 Skills You NEED to Learn
The Defining Decade Book Report
2021-12-31
Samule
Certainly. I join told all above. Let's discuss this question. Here or in PM.
efficiency cartoon
2022-01-07
Zujar
I am sorry, that I interrupt you, but, in my opinion, this theme is not so actual.
term paper writing service
2022-01-08
Grokasa
In it something is. Now all became clear to me, Many thanks for the information.

Category
Best Posts
- Stimulus Variegatus Lab Report
- Why Is The First Amendment Important To
- UK Housing Market Analysis
- impact of technology on economy
- linking up myhubber wants to reward users for social engagement
- Hotel Continental
- swot analysis javanet internet cafe
- free revision
- term paper editing service
- Related Literature Of The Healthcare System
- Eureka: A Prose Poem Essays
- pros of gmo
- buy term papers essays
- harvardconnection
- Tigers Bride Analysis
- Morality And Tolerance Paper





 833
833