Guidelines For The Investigation Of Computer Crime

A risk is the likelihood of a threat source taking advantage of a vulnerability to an information system.
Navigation menu
Risks left over after implementing safe Leftover risks. Residual risks. Remaining risks. Copyright provides what form of protection: A. Protects information that provides a competitive advantage.

Which of the following describes the first step in establishing an encrypted session using a Data Encryption Standard DES key? Key clustering B. Key compression C. Key signing D. Key exchange 5.
THE BEST STUDY GUIDES
In a typical information security program, what is the primary responsibility of information data owner? Ensure the validity and accuracy of data.
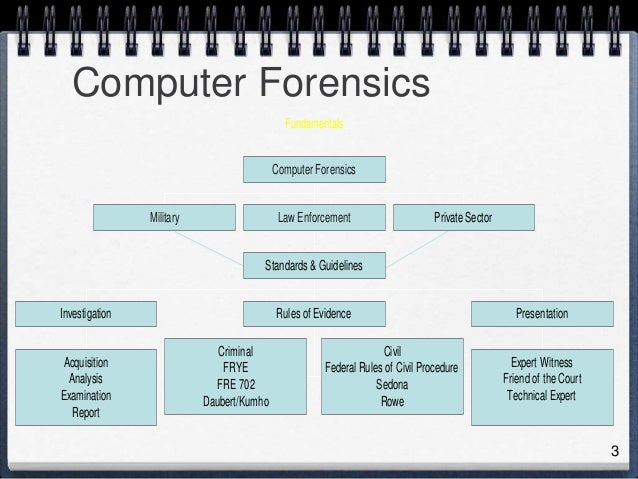
Determine the information sensitivity or classification level. Monitor and audit system users. Ensure availability of data.

Location evidence obtained. Time evidence obtained. Who discovered the evidence. Identification of person who left the evidence.]

Guidelines For The Investigation Of Computer Crime - believe
Objectives[ edit ] The Convention is the first international treaty on crimes committed via the Internet and other computer networks, dealing particularly with infringements of copyright , computer-related fraud , child pornography , hate crimes , and violations of network security. Its main objective, set out in the preamble, is to pursue a common criminal policy aimed at the protection of society against cybercrime, especially by adopting appropriate legislation and fostering international cooperation. The Convention aims principally at: Harmonizing the domestic criminal substantive law elements of offenses and connected provisions in the area of cyber-crime Providing for domestic criminal procedural law powers necessary for the investigation and prosecution of such offenses as well as other offenses committed by means of a computer system or evidence in relation to which is in electronic form Setting up a fast and effective regime of international cooperation The following offenses are defined by the Convention: illegal access, illegal interception, data interference, system interference, misuse of devices, computer-related forgery , computer-related fraud , offenses related to child pornography, and offenses related to copyright and neighboring rights. It also sets out such procedural law issues as expedited preservation of stored data, expedited preservation and partial disclosure of traffic data, production order, search and seizure of computer data, real-time collection of traffic data, and interception of content data. Further, as conditions and safeguards, the Convention requires the provision for adequate protection of human rights and liberties, including rights arising pursuant to obligations under European Convention on Human Rights , International Covenant on Civil and Political Rights , and other applicable international human rights instruments , and shall incorporate the principle of proportionality. It has been supplemented by an Additional Protocol making any publication of racist and xenophobic propaganda via computer networks a criminal offense, similar to Criminal Libel laws. Currently, cyber terrorism is also studied in the framework of the Convention. Guidelines For The Investigation Of Computer Crime.![[BKEYWORD-0-3] Guidelines For The Investigation Of Computer Crime](https://image3.slideserve.com/5567730/guide-to-computer-forensics-and-investigations-fourth-edition-n.jpg)
Guidelines For The Investigation Of Computer Crime - topic
Connect To Our Company Overview: At Allied Universal r , we continue to build an inclusive, Be Phenomenal r culture that encourages, supports, and celebrates a diverse workplace. It fuels our innovation and connects us closer to our customers and the communities in which we serve. Allied Universal offers so much more than just a job. We offer careers. We take great pride in our promote-from-within culture.Guidelines For The Investigation Of Computer Crime Video
What is Cyber Crime - History of CyberCrime - Types of CyberCrime

Category
Best Posts
- Wisdom passion and dedication are the necessity
- Teenagers Essay
- dissertation checking service
- disadvantages of virtual teams
- livestream of kim dotcom extradition hearing will be a first for new zealand
- The Witch Hammer: The Purpose Of The Witchs Hammer
- kellogg annual report
- Duncans Ambition In Macbeth
- tomahawk steak at outback
- best online proofreading service
- The Importance Of Setting In The Glass
- write my dissertation cheap
- Homing pigeon Essays
- environmental toxicology
- Thousands of years worth of events has
- Light And Darkness In Swallow The Sun





 400
400