Computer Security And Social Engineering

Computer security Computer security Each and every one of us is individually responsible for computer security. You may already be taking appropriate security measures without even realising it, but just to be sure have a look at these top tips for computer security. Failure to follow these precautions could result in serious consequences for both the authority and you personally. Workstation and screen Set a strong password.
Personal passwords are Computer Security And Social Engineering first line of defence against attacks on your computer and the council's information systems. This will prevent anyone from accessing the system via your account.
Site footer
Remember, any unauthorised actions carried out on your account would be recorded as being made by you and could result in disciplinary or legal action. Employ a 'Clear Screen' Policy With open plan offices becoming more common, information can easily be read from computer screens. The risk can be reduced by closing any documents or systems containing sensitive information when they are not being worked on and by preventing visitors and unauthorised staff viewing information by angling monitors away from public areas or windows. Emails General emails are not secure, sensitive or confidential information should not be sent by email unless encrypted. When replying to or forwarding an email, ensure that the history does not include unnecessary confidential information or personal email addresses. Remember, your emails may have to be disclosed under the Freedom of Information Act so confine yourself to professional not personal opinions. There is more information and guidelines about sending work emails in the Computer Security And Social Engineering Policy document.

Incoming emails and externally produced documents can contain viruses and worms, be especially cautious of emails which are obviously spam or of an adult nature. These should not be opened but deleted immediately.

Do not click on links embedded within an email without first verifying that the URL is legitimate this can be seen by hovering your cursor over the link and looking for the web address in the notes bottom bar. If you receive a virus alert don't panic!
Navigation menu
Be aware of 'blagging' or Computer Security And Social Engineering engineering' Both these terms refer to the art of manipulating people into performing actions or divulging confidential information. While similar to a confidence trick or simple fraud, the term applies to unlawful information gathering or computer system access. If you are unsure whether a telephone call, email or visitor is genuine, do not divulge any information until you are sure the recipient is authorised to have that information. Recognise how to spot 'phishing' attempts Phishing is the fraudulent process of attempting to acquire sensitive information such as usernames, passwords and credit card details, by masquerading as a trustworthy company or organisation in Budget Cuts electronic communication. Communications claiming to be from commercial companies such as banks, PayPal, or eBay are commonly used to lure the unsuspecting, often directing users to input their information onto a fake website.
Banks and online companies do not send emails asking their customers to reveal personal information or security details. Ignore and delete any such messages. You should also be aware of other public sector bodies, partnership agencies or charities asking for similar information. Browse the internet securely Be wary of any website that isn't known to you.
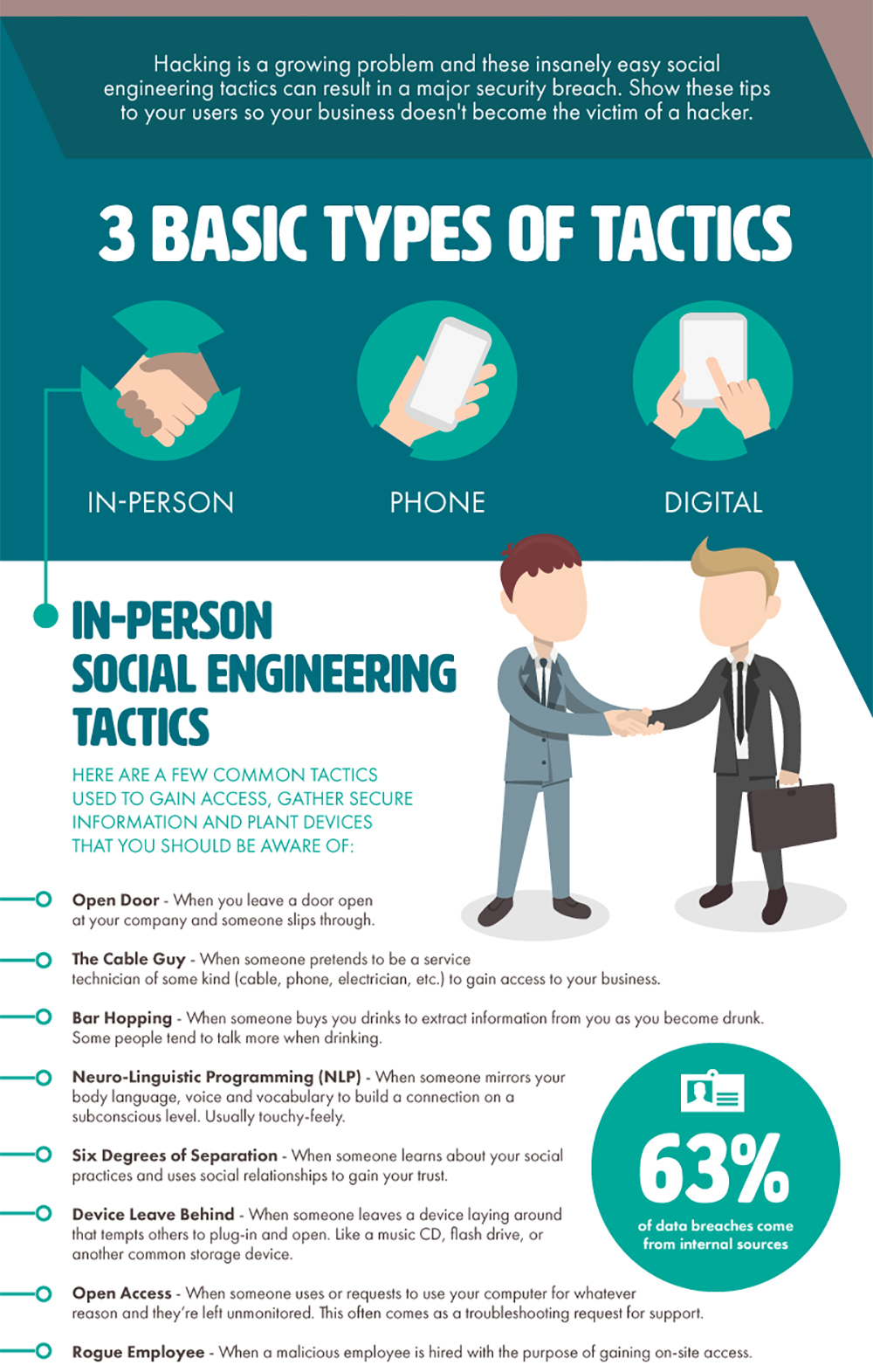
Things to look out for include predominantly Computer Security And Social Engineering or very dark coloured web sites, text styles that don't seem right, information that seems to serve no particular purpose or that doesn't tie in with the purpose of the site. If you feel at all uneasy about a web site, leave it immediately by clicking the Back button on your web browser or by closing your web browser. Avoid any pop-ups that appear.]
Excited: Computer Security And Social Engineering
| A CASE GUIDE OF THE GLOBAL BEER | 729 |
| ESSAY ON THE MANSION IN THE GREAT GATSBY | 2 days ago · Social engineering is when a criminal manipulates an individual or company into giving up confidential information. They may attempt to seek out numerous types of data including your passwords, bank or other financial information.. With password security becoming stronger, criminal s are now rely ing on the trusting nature of human beings to give up information or give them access to company. 3 days ago · Wait a minimum of ten days after reaching the United States to apply for a Social Security card. Register for classes (full-time or certified full-time). Get the Certificate of F-1 Student On-Campus Employment for Social Security Number Application from ECE and have it further certified by the ISSO. This form is required to apply for a Social. 9 hours ago · Emerging Paradigms of Computer Science Engineering. ‘Digital’ – this small word has become the axis on which the whole world revolves nowadays. People, who were not aware of the power of digitization, now understand it after most of the significant activities in every field shifted to digital amid the COVID outbreak. |
| Computer Security And Social Engineering | 832 |
| Communication accommodation theory examples | 3 days ago · Wait a minimum of ten days after reaching the United States to apply for a Social Security card. Register for classes (full-time or certified full-time). Get the Certificate of F-1 Student On-Campus Employment for Social Security Number Application from ECE and have it further certified by the ISSO. This form is required to apply for a Social. 2 days ago · 98% of cyber attacks have some form of social engineering involved Social engineering is a way of influencing, manipulating or deceiving people to control their computer systems. Social engineering tactics may include emails (phishing), snail mails, phone calls, direct personal contact. Here are some examples. 9 hours ago · Emerging Paradigms of Computer Science Engineering. ‘Digital’ – this small word has become the axis on which the whole world revolves nowadays. People, who were not aware of the power of digitization, now understand it after most of the significant activities in every field shifted to digital amid the COVID outbreak. |
![[BKEYWORD-0-3] Computer Security And Social Engineering](https://www.offgridweb.com/wp-content/uploads/2017/01/Social-engineering-phishing-security-computer-crime-infographic-6.jpg)
Computer Security And Social Engineering - opinion
Cyber Tom Barton, August 3 2 mins Digital Marketing Manager In the last 12 months, four in ten businesses and one in four charities have reported having cyber security attacks or breaches. This is according to a report published by the UK government in March With COVID and nationwide lockdowns, cyber criminals targeted more companies and businesses using social engineering and other methods ever recorded. But what exactly is social engineering? What is social engineering? Social engineering is when a criminal manipulates an individual or company into giving up confidential information. They may attempt to seek out numerous types of data including your passwords, bank or other financial information. With password security becoming stronger, criminals are now relying on the trusting nature of human beings to give up information or give them access to company platforms and accounts. What are the different types of social engineering? There are several different types of social engineering which a cyber-criminal may use to extort data or information from you.

Category
Best Posts
- Shrek and His Modern Princess
- organizational health inventory
- Product Line Selection Model Essay
- Importance Of Passion In Education
- The Brief Wondrous Life Of Oscar Wao Essay
- elizabeth proctor essay
- c wright mills the promise pdf
- The Importance Of Choices
- Failure To Wear Eye Makeup In Ancient Egypt
- Burro Genius Veillasenor Character Analysis
- Sonnys Blues Theme Analysis
- Duvaliers Impact On Haiti Today
- Essay About My Head Was Spinning All
- Racial Profiling Argument





 1157
1157