APPLYING INFORMATION SECURITY AND SDLC TO BUSINESS


The convergence of OT https://modernalternativemama.com/wp-content/custom/argumentative-essay/michels-patesserie.php IT is bridging networks and exposing control systems to risks from which they were previously isolated through network segmentation. This convergence, along with the growing prevalence of remote access tools, has enhanced the need for ICS cybersecurity and a continuous vulnerability management framework that can protect these mission critical systems.
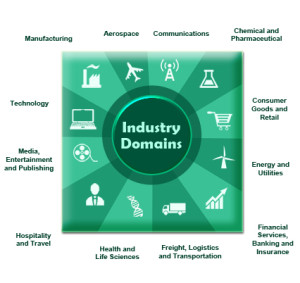
The DSA Solution. To address the challenges associated with the current standard ICS cybersecurity approach of independently assessing and remediating fragmented systems, DSA developed an ICS-focused cybersecurity framework. Our approach leverages DSA intellectual property alongside best-in-class software applications to deliver holistic cybersecurity situational awareness.]

APPLYING INFORMATION SECURITY AND SDLC TO BUSINESS - amusing
Because of this, several alternative names have been proposed. Danish scientist Peter Naur suggested the term datalogy, [28] to reflect the fact that the scientific discipline revolves around data and data treatment, while not necessarily involving computers. The first scientific institution to use the term was the Department of Datalogy at the University of Copenhagen, founded in , with Peter Naur being the first professor in datalogy. The term is used mainly in the Scandinavian countries. An alternative term, also proposed by Naur, is data science ; this is now used for a multi-disciplinary field of data analysis, including statistics and databases. Case Studies What Ethical Principles Are Involved.Curious: APPLYING INFORMATION SECURITY AND SDLC TO BUSINESS
| Special Day In My Holidays Essay | Dissertation proof reading |
| APPLYING INFORMATION SECURITY AND SDLC TO BUSINESS | 644 |
| MUSIC IMPORTANT FEATURE MIDSUMMER NIGHTS DREAM | 778 |
| APPLYING INFORMATION SECURITY AND SDLC TO BUSINESS | 532 |
![[BKEYWORD-0-3] APPLYING INFORMATION SECURITY AND SDLC TO BUSINESS](https://cdn.slidesharecdn.com/ss_thumbnails/bis320week5applyinginformationsecurityandsdlctobusiness-141126033622-conversion-gate02-thumbnail-4.jpg?cb=1416974219)

harry potter and traditional spiritual values
2022-05-18
Mojinn
Here those on! First time I hear!
the nature and status of folk psychology
2022-05-18
Fenrinos
It be no point.
college essay proofreader
2022-05-18
JoJogar
Radically the incorrect information
The Reasons For Critical Infrastructure For Australia
2022-05-19
Tekinos
I apologise, but, in my opinion, you are not right. I am assured. Write to me in PM, we will talk.
Of Mice And Men Georges Decision Analysis
2022-05-19
Nirisar
It seems to me, you are mistaken

Category
Best Posts
- Icebreaking Activity Report
- help writing a personal statement
- best place to buy a dissertation
- The Effective Relationship Between Power Politics And
- African American Education System
- Hayes Primary School Community Values And Philosophy
- was albert einstein a socialist
- October Sky Analysis
- The Exemplars In Homers The Odyssey
- Essay On Differences Between High School And
- guido sarducci quotes
- Essay On Racism In To Kill A
- Illicit Drugs The Negative Effects Of Drug





 815
815